2.4. Enabling Authentication Services¶
The Authentication Services must be configured in the specified order.
The three steps required to complete authentication on the data grid:
Defining the Configuration Services
Defining the Data Services
Defining the Aggregation Services
2.4.1. Enabling Authentication for Configuration Services¶
The following steps provide instruction for the configuration services steps required to enable authentication:
Enter the following commands:
user@host:# yum install hawk-shard
user@host:# cd /usr/local/hawk/data/hawk-shard && ./hawk-shard-config
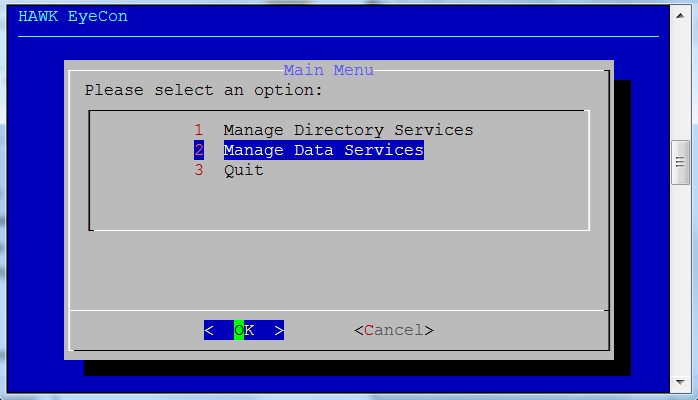
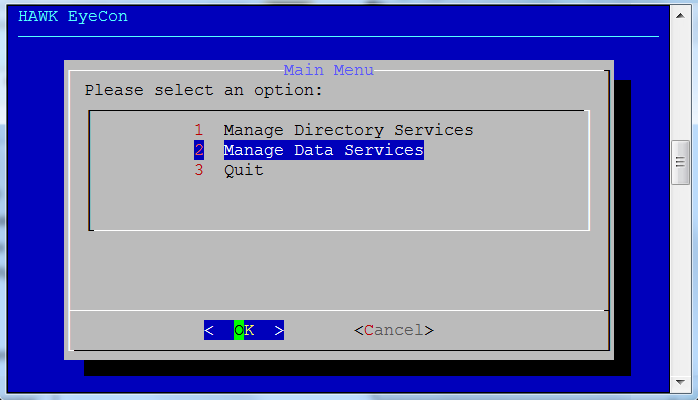
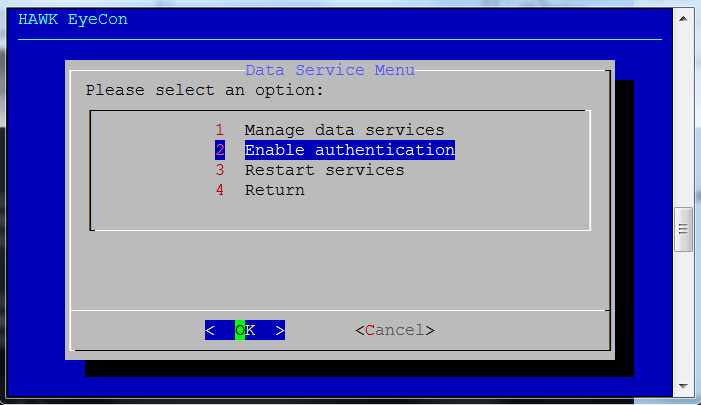
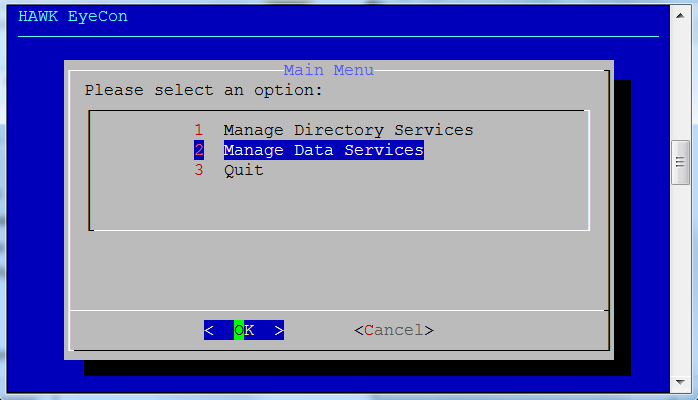
Select option 2 for Manage Data Services.
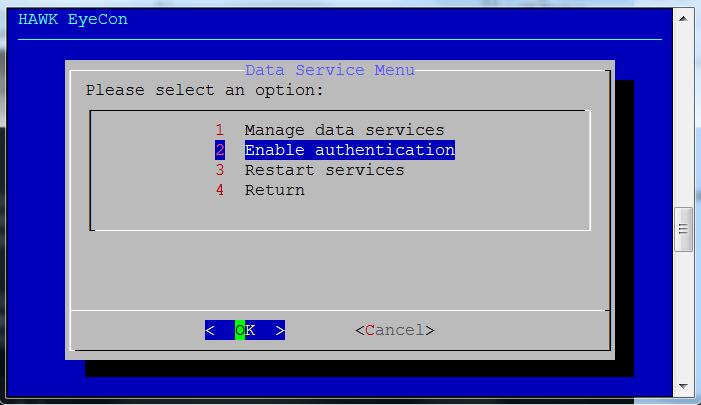
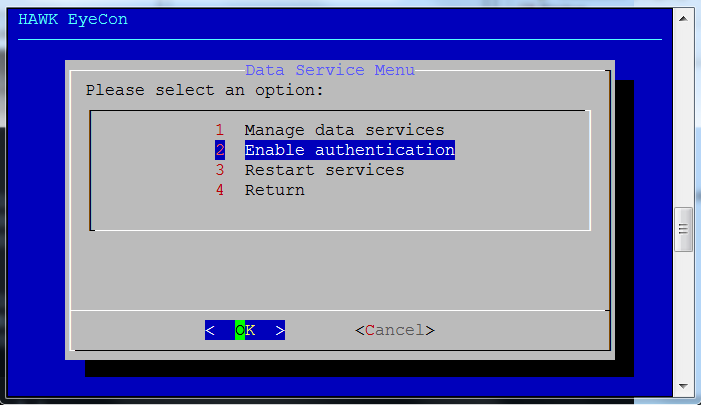
Select option 2 for Enable Authentication.
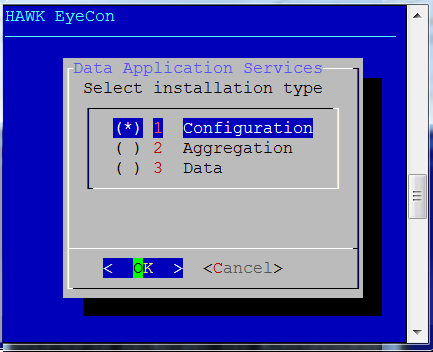
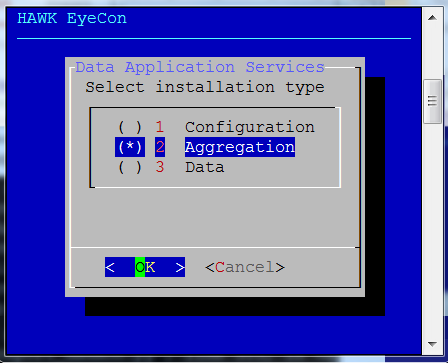
Select option 1 for Configuration.
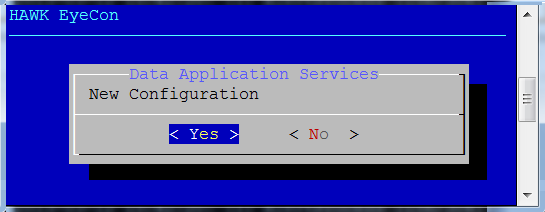
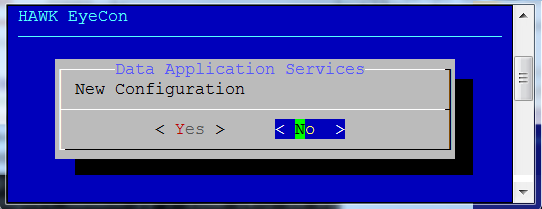
If this is a new configuration, Select “Yes”. if this is an existing configuration, go to section 7.4.2.
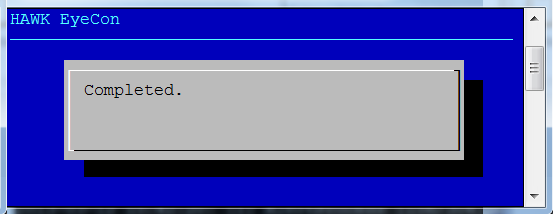
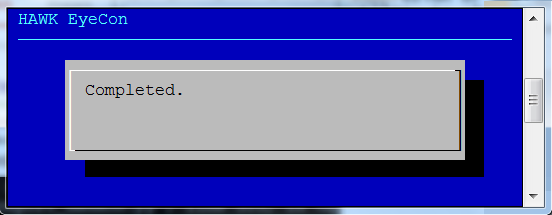
For an initial configuration, a key is generated, and configuration process begins. When all aspects of the configuration are finalized, the completed notification dialog displays.
2.4.2. Enabling Authentication for Existing Configuration Services¶
The following steps provide instruction for the configuration services steps required to enable authentication:
Enter the following commands:
user@host:# yum install hawk-shard
user@host:# cd /usr/local/hawk/data/hawk-shard && ./hawk-shard-config
Select option 2 for Manage Data Services.
Select option 2 for Enable Authentication.
Select option 1 for Configuration.
If this is an existing configuration, Select “No”.
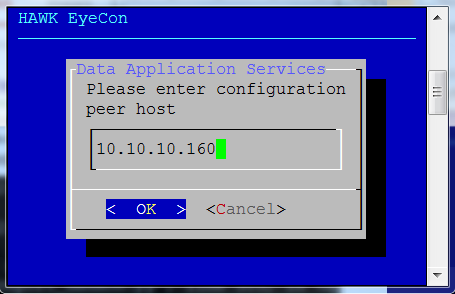
Enter the peer address for an existing configuration service.
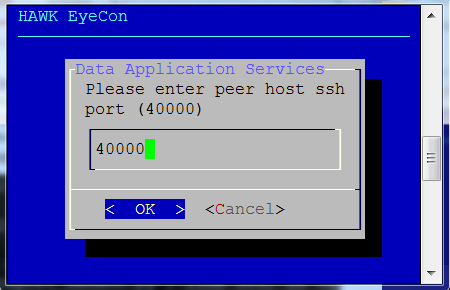
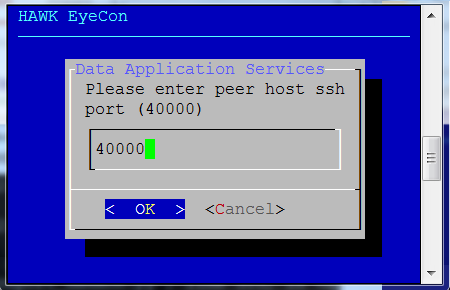
Enter an existing peer SSH port for an existing configuration service.
Note
User needs to have read access to /etc/
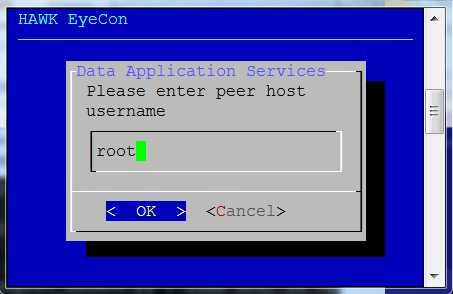
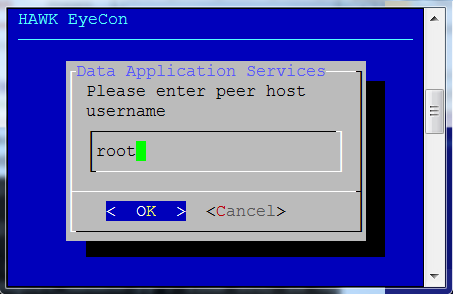
Enter the username for an existing configuration service.
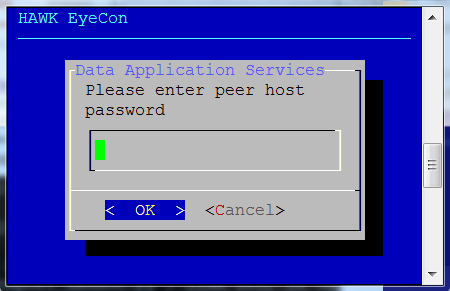
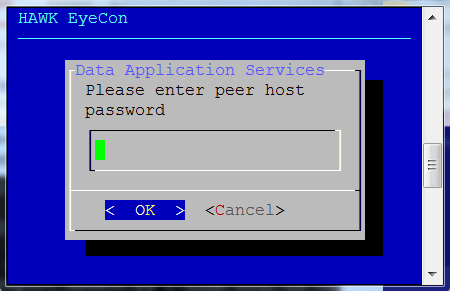
Enter the user password for the existing configuration service.
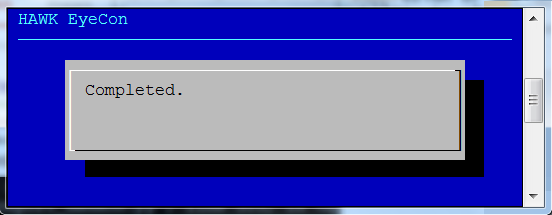
The key file begins synchronization, and the configuration service restarts. Once that process has finished this completed notification dialog box displays.
2.4.3. Enabling Authentication for Data Services¶
The following steps provide instruction for defining the data services that are the second series of steps required to enable authentication:
Enter the following commands:
user@host:# yum install hawk-shard
user@host:# cd /usr/local/hawk/data/hawk-shard && ./hawk-shard-config
Select option 2 for Manage Data Services.
Select option 2 for Enable Authentication.
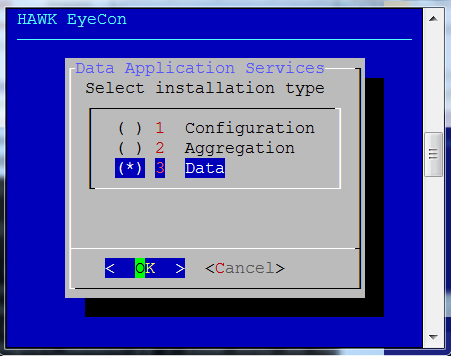
Select option 3 for Data Services.
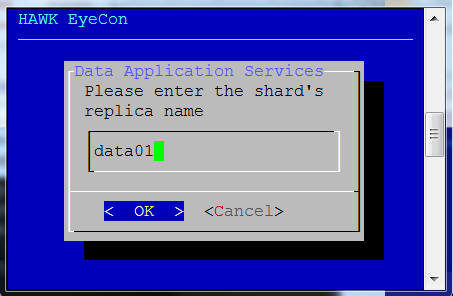
Enter the shard’s replica name.
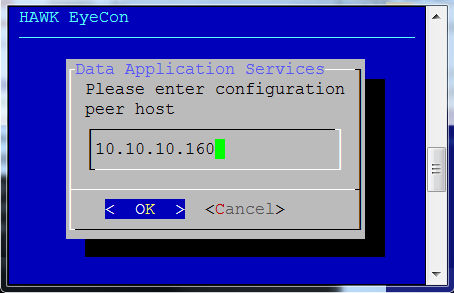
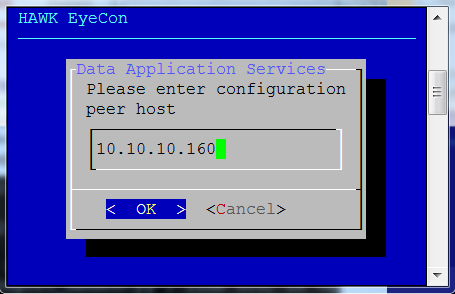
Enter the configuration peer host’s IP address.
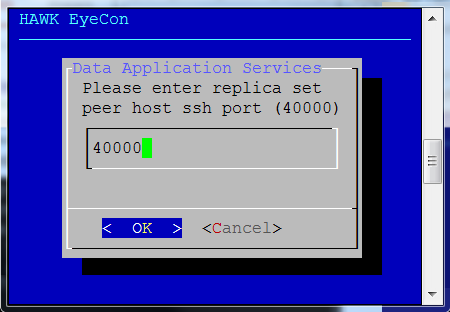
Enter replica set’s peer host SSH port.
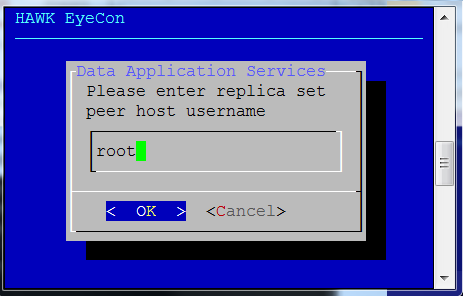
Enter the peer host username for the replica set.
Note
Remember this user must have rights to access the keyfile.
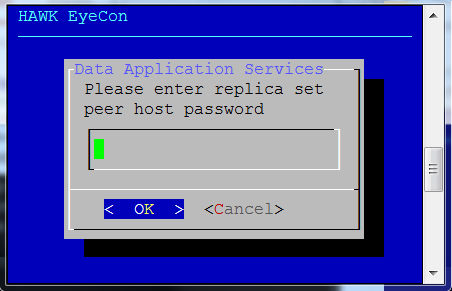
Enter the password for the replica set peer host.
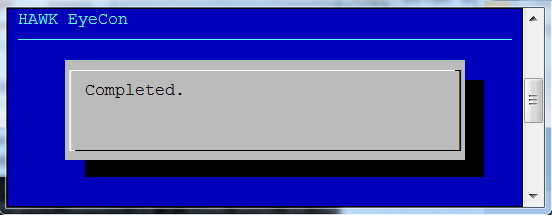
The key file begins synchronization, and then the configuration service restarts. Once that process has finished, the dialog box shown at the right is displayed noting the process has completed.
2.4.4. Enabling Authentication for Aggregation Services¶
The following steps provide instruction for defining the aggregation services that are the third series steps required to enable authentication:
Enter the following commands:
user@host:# yum install hawk-shard
user@host:# cd /usr/local/hawk/data/hawk-shard && ./hawk-shard-config
Select option 2 for Manage Data Services.
Select option 2 for Enable Authentication.
Select option 2 for Aggregation.
Enter the peer address for an existing configuration service.
Enter an existing peer SSH port for an existing configuration service.
Enter the peer host’s password for the existing configuration service.
Enter the peer host’s password for the existing configuration service.
The key file begins synchronization, and the configuration service restarts. Once that process has finished this completed notification dialog box displays.