7. Working with the Tools¶
When analysts are investigating a potential threat, there are a variety of tools that allow the domain name to be looked up, the route to be traced, and the ability to determine if the originating system is still active. The Tools section provides a variety of methods to perform these tasks.
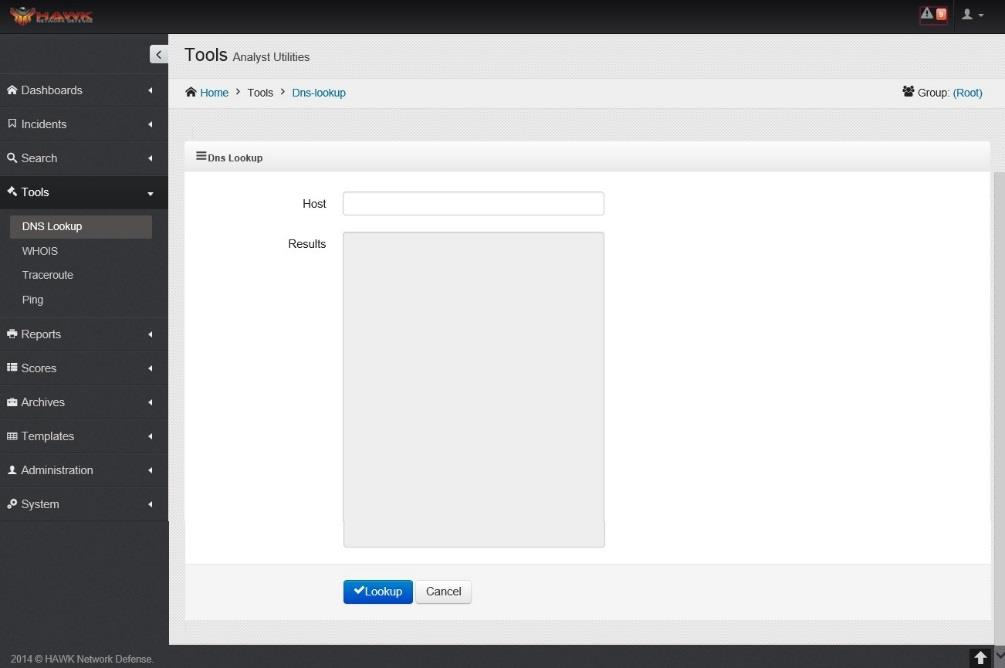
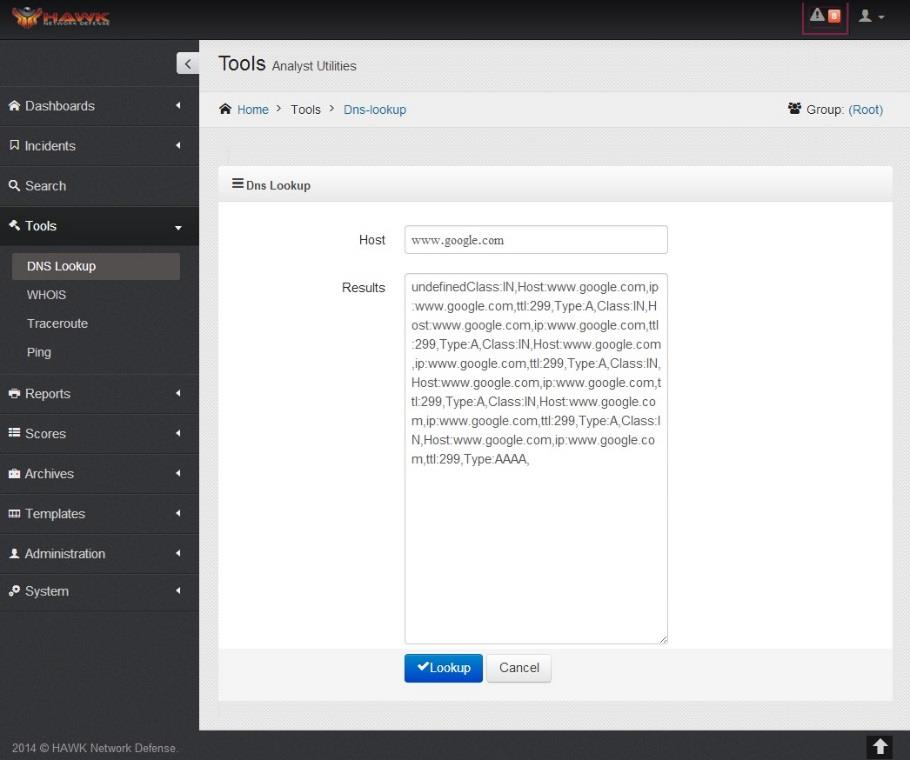
7.1. Using DNS Lookup¶
A DNS lookup is a tool used to determine the Domain name records and IP address associated to the Domain name. DNS lookup can be accomplished on the HAWK eyeCon by following these steps:
On the navigation panel, click on .
Enter the Domain Name in the Host field.
Click on the button.
The response is shown in the Results section.
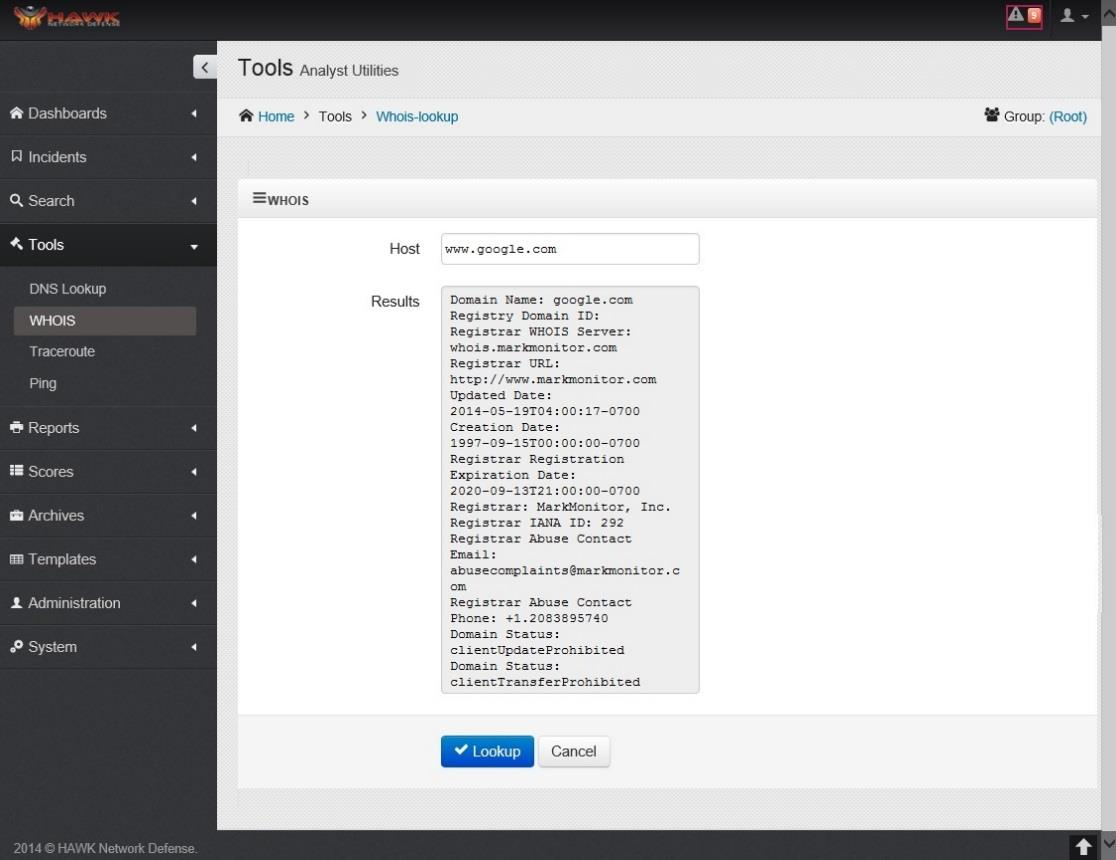
7.2. Using WHOIS¶
When a domain name is registered through the Internet Corporation for Assigned Names, and Numbers, (ICANN), the person submitting the request for the domain name has to provide personal contact information which includes name, address, phone number, E-Mail address, etc, in order to register the domain name. ICANN maintains a database of all the domains around the world. This database contains the contact information as well as the expiration date of the domain, if ownership of the domain has been transferred to another group, and a variety of other information regarding the domain.
These domains can be public or private, and if they are public, their full contact information is open to anyone who wants to find who owns the domain. If the domain is registered as private; then a proxy is used to protect the privacy of the owners, and there are various companies who will act as a proxy, which means anyone looking up the WHOIS information only gets as far as the information on the proxy. It’s designed to protect the owners from data miners, spammers, hackers, and other potential threats.
The HAWK Tools section provides an easy way of performing a WHOIS database search by following these steps:
On the navigation panel, click on .
Enter the Domain Name in the Host field.
Click on the button.
The response is shown in the Results section.
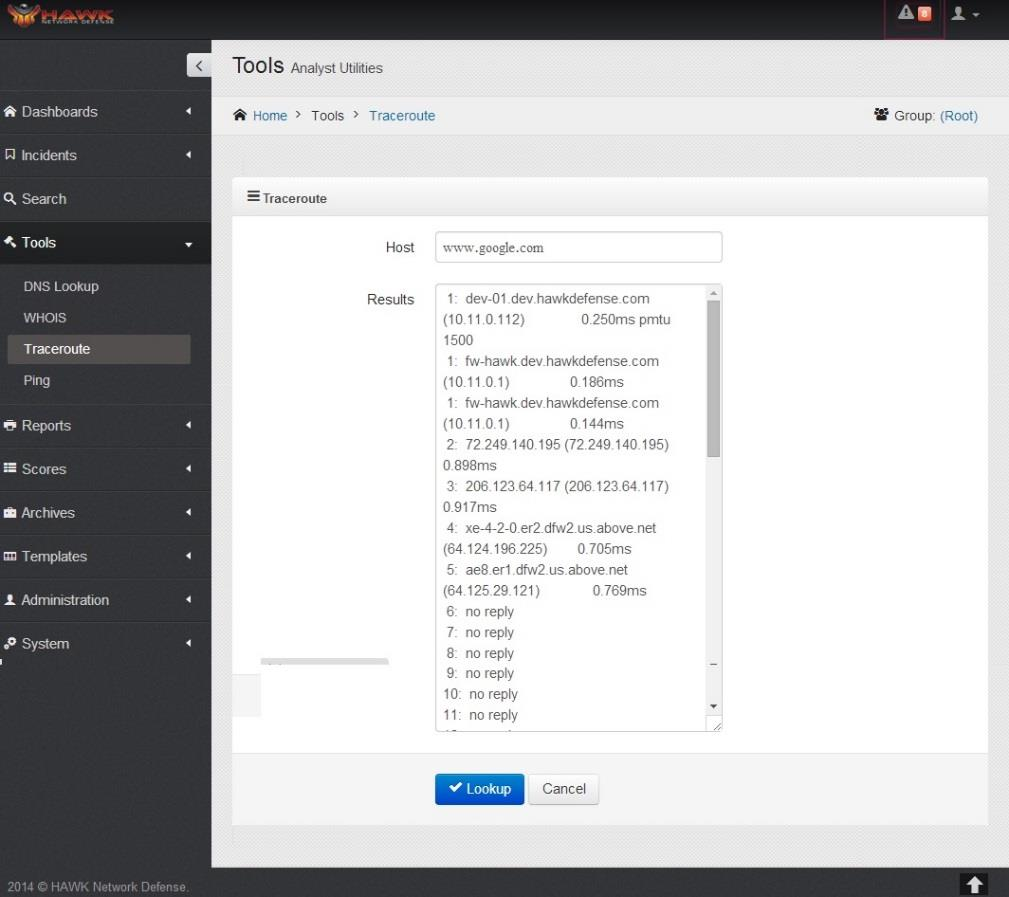
7.3. Using Traceroute¶
As the analysts is trying to determine where the threat, or malicious access, started, another tool that is very helpful is traceroute. This utility helps the analyst in tracing the route to the specific gateway computer where the threat originated, and trace the path through the network to this origination point. This utility initiates the trace by sending a packet using the Internet Control Message Protocol (ICMP) which uses a Time Limit value to trace back to the previous hop or router. This helps determine the amount of time it took to hop to the first router. Next, it resends the package with a different Time Limit value to the second router in the path, and continues in this manner until it has proceeded through the route to the originating system. This allows the analysts to follow the entire route of the threat from the source to the destination.
HAWK provides a Traceroute tool with the Tools Dashboard, which can be used by following these steps:
On the navigation panel, click on .
Enter the Domain Name or IP address in the Host field.
Click on the button.
The response is shown in the Results section.
7.4. Using Ping¶
Another tool that analysts use to investigate a malicious threat is Ping. This is a diagnostic tool that determines if the IP address is actively works and it tests connectivity to the source by sending an Internet Control Message Protocol (ICMP) Echo Request. It waits a designated time period for a reply from the distant end, and determines the response time it takes for the distant end to acknowledge the request. This helps determine if the IP address entered is active.
HAWK provides the Ping tool in the Tools Dashboard, which can be used by following these steps:
On the navigation panel, click on .
Enter the Domain Name or IP address in the Host field.
Click on the button.
The response is shown in the Results section.